What’s the true cost of Cybercrime and How to Protect Yourself
Read the information below and you’ll soon answer yes to this question: Isn’t it Time to Move Beyond Your Parent’s Internet?
The internet or the World Wide Web got its start in the late 1990s. I was at MCI when we introduced the internet to our consumers and businesses. Vint Cerf, known as “the Father of the Internet” who was the co-designer of TCP/IP protocols and the architecture of the Internet, was an executive at MCI, whom I took out on client calls.
But that was almost 23 years ago. The internet has become our defacto mode of doing almost everything. Now, the whole world is a gigantic cyber village with hackers and characters who have surpassed what that old technology can handle.
The internet is now “the Exposed Web” and it has become a dangerous place to search, transact, and also store your information on apps. Everything that we do there is tracked, data that is shared there can be hacked or exposed, our identities can be stolen and client records are breached.
There’s no doubt about it, whether you’re an individual or a business, with Web 2.0, you’re exposed.
The Cybercrime Statistics Worldwide Are Frightening, But Why Aren’t We Taking Action?
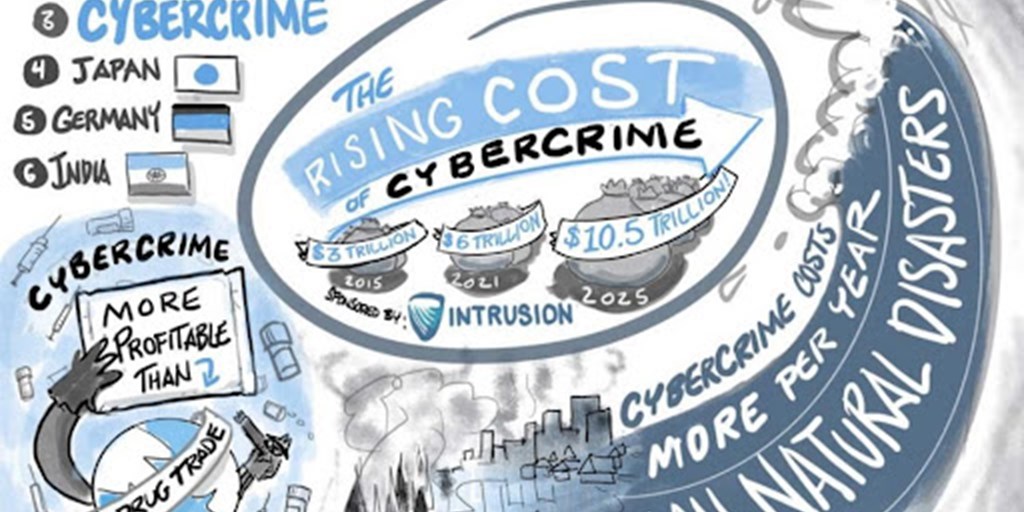
Why Cybercrime is a problem? Cybercrime hits every person and every business that enters the internet. Just look at the statistics from Cybersecurity Ventures in this visual which shows the economic impact of cybercrime:
- $10.5 Trillion dollars in Internet Fraud by 2025, almost 2x over 2020 in 5 years.
- Cybercrime is more profitable than All of the Global Drug Trade combined
- Cybercrime ranks #3 in size behind the US and China’s economies
- In the U.S. 15 million people will get their identities stolen this year
- 33% of the U.S. has already had their identity stolen
In the movie Jaws, I was a poor parent and watched it with my two kids. My daughter, who was in junior high at the time said, “Why doesn’t she get out of the water when she hears that music?” I still think that one is funny. It’s so obvious, right?
Well, the exposure and risks on the internet are so obvious, but we just log in and do business as usual. I’m now sounding the Jaws music, it’s now unsafe to get into the water…GET OUT. An attack is lurking there for everyone and like in Jaws, it can have devastating consequences.
Identity Theft, a Scary Tale for Everyone
- In the U.S. 15 million people will get their identities stolen this year
- 33% of the U.S. has already had their identity is stolen (FTC)
- Every 14 seconds another individual in the US has become a victim
- 49 million people were a victim in 2020 costing $56 billion in 2020 (Javelin)
- The FTC reported that 2.2 million fraud reports were filed in 2020.
Unfortunately, unscrupulous characters are getting bolder attacking individuals directly with phishing emails and direct-interaction scams reported Javelin. Imposter fraud is at the top of the FTC list, showing the important need for KYC and authenticating individuals. Before clicking on a link, make sure you know who it’s from, or better yet, run it through the ORBITi search to see if it’s an authenticated business or a fraudulent scam.
Key Hacking Statistics
- Verizon reports that phishing attempts account for over 80% of malware infections and over 95% of espionage attacks. (So, watch what you click on!)
- Ransomware attacks happen every 14 seconds.
- 43% of cyberattacks hit small businesses.
- Phishing emails account for 91 percent of cyberattacks against enterprise companies.
Who is Most Affected of Cybercrime? Beware of Social Media!
HubSpot reports that 47% of social media respondents have seen an increase in spam in their newsfeeds. Of these, 79% include fake news or cybercrimes. Ads, fake news, and other content which is intended to lead you to a hacker’s website. Beware of their requests for personal information, which are routinely connected with automatic malware downloads.
Email – Watch What You Click On
- The UK Department for Digital, Culture, Media & Sport reports that 75% of respondents who suffered a cyberattack were initiated through a fraudulent email. Businesses still are seen as easy prey to hackers.
- Retruster reports that 30% of U.S. users open phishing emails, and 12% of those click on infected links with cyber security threats.
- CyberArk’s study showed that of 1,300 IT decision makers, 56% stated that phishing attacks were their greatest threat from employees clicking on links.
Centralized Databases Are Breached at an Alarming Rate.
Centralized databases have been around for about 50 years. They host client data in a repository, it’s usually in one or two places and just sitting there with a target on its back. Hackers find their way in and it usually takes many months for most companies to realize that their data has been hacked.
In 2021 there were over 37 billion data records exposed from some of the top enterprise companies around the world. Think your data wasn’t exposed? Think again, if you were a LinkedIn subscriber, 92% of subscriber information was exposed, over 700 million users!
Top Data Breaches in 2021:
- Comcast (1.5 billion)
- Brazilian resident data leak (660 million)
- Facebook (533 million)
- LinkedIn (500 million)
- Bykea (400 million)
Apps Are a Smorgasbord Menu for Hackers
We think of our apps as secure places to conduct our business and to hold the data that is used within the app. We also assume that because an app might come from a large enterprise, they have encrypted the data and protected us. Unfortunately, hack after hack, this is not the case. Again, it goes back to the flaw of Centralized Databases from the section above.
Microsoft Teams - Just this week, the headlines showed that “Microsoft Teams deemed unsafe to use by security researchers”. The cybersecurity research firm Vectra found a flaw providing vulnerability to a third-party attack.
Let’s review some other exposures, the first one is very alarming:
- 92% of the top 100 paid Apple iOS apps and 100% of the Top 100 paid Android apps have been hacked, according to a recent report by Arxan Technologies.
- “Dropbox links sharing Syndrome” – According to the Ponemon Institute, 85% of companies use services like Dropbox to share links, which are also shared outside of the company and expose important company data.
- DocuSign shares contracts via unsecured links via email. Emails can be shared or hacked and again, anyone can open an unsecured link, sign a contract and cause a future legal issue that wasn’t intended.
Unless you have a secure way
The Average Cost of a Data Breach (the true cost of cybercrime)
In an IBM’s Report, “How Much Does a Data Breach Cost in 2022”, they reveal these statistics:
- The average ransomware breach costs $4.62 million
- The average data breach costs companies $4.24 million
- Healthcare breaches increased by 29.5% in 2021
- Lost business opportunities cost $1.59 million
- 39% of costs are incurred more than a year after the breach
How Working Remote is a Factor in Data Breaches
Working remotely has a documented 35% productivity gain for employers. Conversely, remote workers represent a higher risk for data breach activity. The same IBM study showed:
- The total cost of a data breach was $1 million higher when working remote
- Organizations with 60 percent remote workers had a higher average data breach cost than those without remote workers.
In the Real World from Here Live casts Tim and I have shared many new statistics on “Work from Anywhere” and the many wonderful benefits. We have also shared that an overwhelming majority of businesses still don’t have a remote working strategy or digital plan for protecting themselves. With all of the factors addressed above, it’s now time to take action!
How Do I Protect Myself from Digital Fraud?
The answer is by moving to a new internet. The current internet is rife with so many issues that just can’t protect you or your business. Apps and Centralized data storage expose your data. The costs are just too high for you and your customers.
The future is in blockchain, authentication, private web browsers, setting up your own private web and accessing decentralized apps that can only be accessed via a private key. BlockCerts spent 2-million-person hours in developing all of these tools and hashed to the first authenticated internet. You don’t have to be a developer; you don’t have to hire a large staff to create something for your company.
Step 1: Download the ORBITi Private Browser at BlockCERTS.com
- You will no longer be tracked by any company and your data can’t be sold to anyone
- Stop Phishing attacks. Before you click on any link in an email, copy and paste it into the ORBITi browser to see if it’s safe.
- Stop Spoofing by checking on any business website to see if it is authentic or fake.
Step 2: Download the BCERTin Wallet – You’ll be prompted once you’ve set up your ORBITi. Simply set up your private vault, follow the steps to authenticate yourself, and get your private key. Now you have a private cloud. It’s your own private internet.
Step 3: Use the Apps in your BCERTin Wallet for privacy and safety AND to eliminate your current costs from individual apps that are exposing your data! For about $9 a month, you’ll save $100 or more monthly, over $1,000 a year!
Step 4: Register your Web 4.0 Private Domain Name at DomainCERTin.com. It shows that you are an authenticated business. You can use this name for branding and use it everywhere. Hurry while these domains are still available!
Isn’t about time to protect yourself, and your business and put the control back in your hands forever?
To enable comments sign up for a Disqus account and enter your Disqus shortname in the Articulate node settings.






